The Root DNSSEC KSK (Key-signing Key) Ceremony is a strict procedure during which the DNS root zone’s public keying information is signed for the three months following it. The KSK is the key used to sign the set of Zone-signing Keys (ZSK) every three months; being the trust anchor of the Domain Name System (DNS). As the ZSKs are used to digitally sign the DNS root zone.
Since 2016, the DNS root zone is overseen by ICANN (Internet Corporation for Assigned Names and Numbers), which delegated the DNS root zone’s management to IANA (Internet Assigned Numbers Authority). IANA is the organization that keeps the private portion of the Key-Signing Key locked away.
In addition, Verisign is responsible for the DNS root zone maintenance. It is in charge of generating the Root Zone-signing Key which is signed during the ceremony.
What’s the goal of the Root Key-Signing Key Ceremony?
Since the DNS root zone has no parent zone, the Root DNSSEC KSK Ceremony takes place to reinforce trust and ensure the integrity and authenticity of the DNS root zone’s information. The DNS root zone contains information about how to query the top-level domain (TLD) name servers, such as “.com”, “.org” and “.edu”, allowing Internet users to access domain names in all TLDs. So, its reliability is essential.

Security and transparency
The Root Signing Ceremony is public and broadcasted on live streaming, to reinforce trust and transparency. The ceremony is firmly controlled and audited. The strictest security is necessary for the DNSSEC protocol to succeed as a global standard.
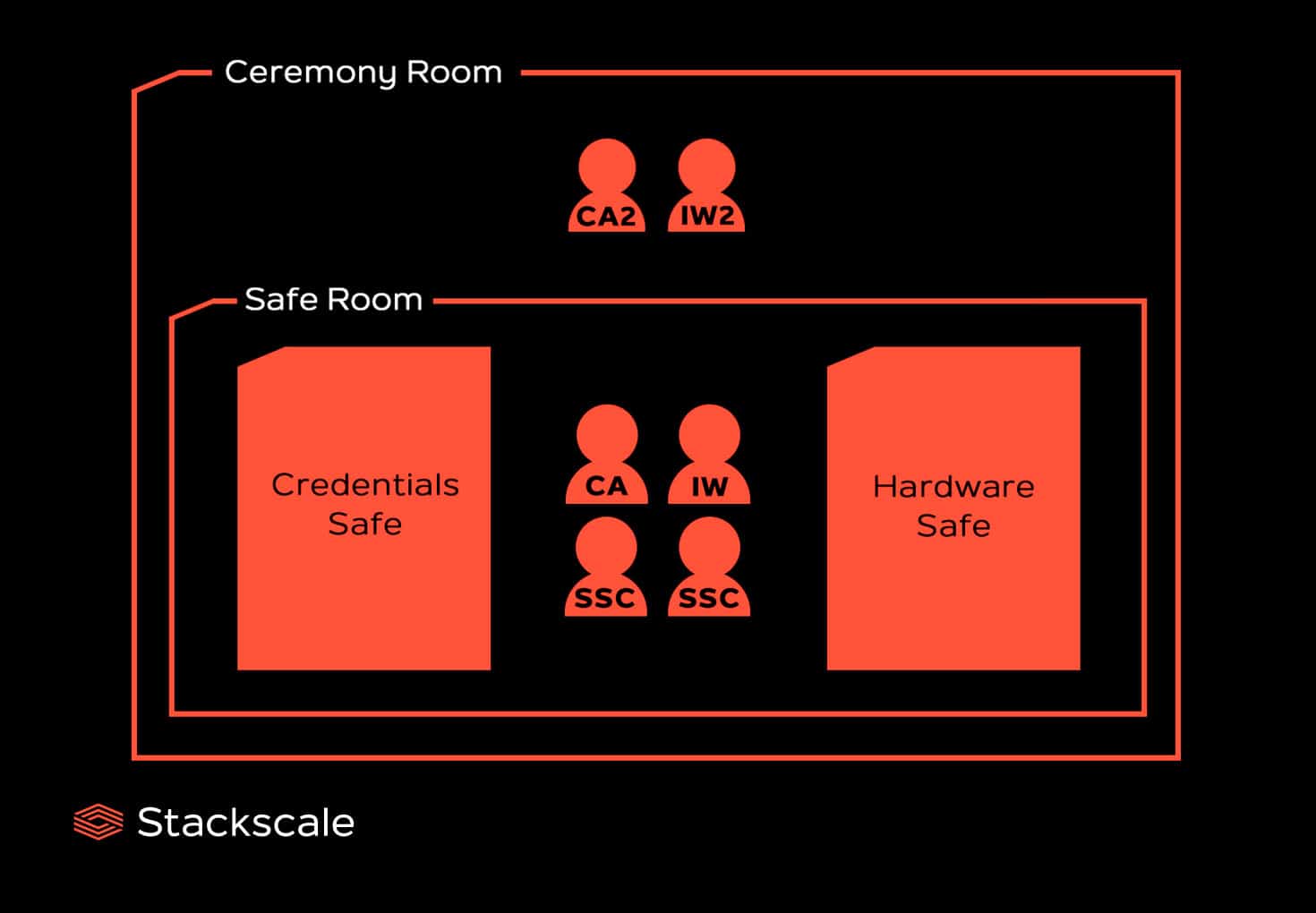
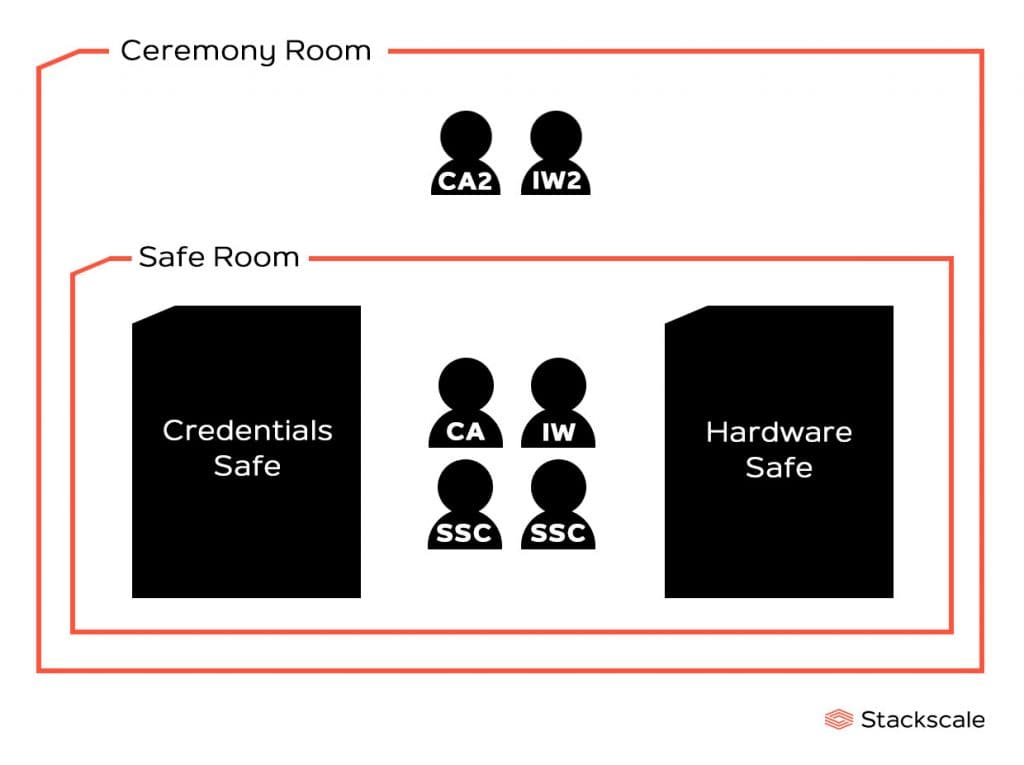
Every precaution is taken to minimize the risk of malicious conspirators. In the ceremony room, within a safe room, there are two safes to separate the access to the Hardware Security Module (HSM) from the access to the operators’ cards that activate it. One safe keeps the credentials to activate the HSM, inside plastic cases in tamper-proof bags, and the other one keeps the HSM and the private portion of the KSK.
In order to keep the chances of conspiracies that could compromise the KSK to the minimum, the ceremony is divided in several parts and the roles of each participant is thoroughly defined. Participants go through a series of steps and checks to cryptographically sign the digital key pairs that are used to secure the DNS root zone.
Moreover, participants must pass through a number of security layers, such as access cards and fingerprint and retina scans for getting into the ceremony room. Everything is audited by two auditing firms that aren’t associated with Verisign or ICANN and when the ceremony is complete, all pieces are returned to their respective safes, sealed, and everyone leaves the room. In addition, during these ceremonies, other operations, such as replacing hardware, installing new cryptographic officers or generating or replacing a KSK, can be performed if necessary.
Who participates in the Root Signing Ceremony?
The following list represents the minimum sets of participants necessary to complete the Root Signing Ceremony:
- The Ceremony Administrator (CA), who is responsible for executing the ceremony as planned in the script.
- The Internal Witness (IW), who ensures that the CA follows the script dutifully. He also records any deviation from the script through an exception reporting.
- The Second Ceremony Administrator (CA2) and the Second Internal Witness (IW2), who aid in logistics and guarantee dual-occupancy rules to be satisfied in the ceremony room, while the CA and the IW are in the safe room. They can come to replace them if they aren’t able to fulfill their roles.
- 2 Safe Security Controllers (SSCs), who open the two safes in the ceremony room.
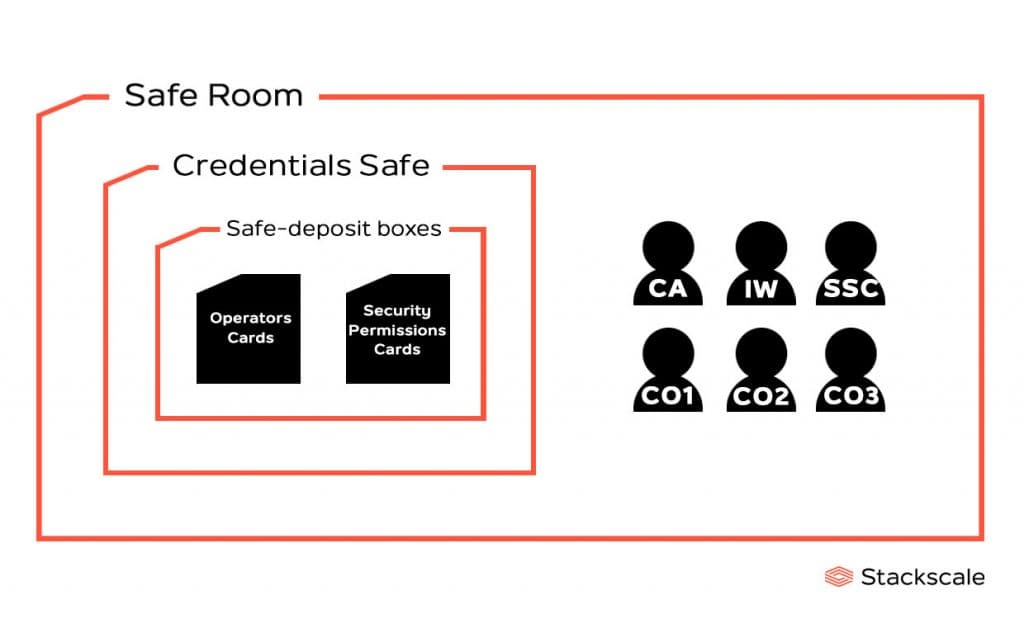
- 3 Crypto Officers (COs), who have the keys to the safe-deposit boxes inside of the Credentials Safe for taking 3 of the 7 smart-cards required for activating a given HSM. Each deposit box is open by two keys: the CA has one of the keys and each of the COs has a key to one of the safe-deposit boxes. COs are trusted volunteers from the Internet community and, as such, they also act as witnesses and attest that the ceremonies are conducted properly.
- A third-party auditor, who represents the organization that audits the ceremony for compliance.
- A ZSK representative, who represents the Root Zone Maintainer, in charge of maintaining the Root Zone-signing Keys.
- The Root KSK Operations Security (RKOS),who schedule, plan and execute the ceremony, as well as provide logistical support. They are staff from the Cryptographic Business Operations team responsible for managing the Key-signing key.
- The System Administrator (SA), who operates the support systems used during the ceremony and can resolve technical failures that may arise.
In any case, to minimize cancellation risks, there must be additional staff available. For instance, COs are polled to find a two-day window when at least 4 of them are available.
In addition, as it is a public ceremony, anyone can request to attend the DNSSEC Root KSK Ceremony as an observer. However, as space in the ceremony room is limited, there aren’t many seats available. For attending it, observers must submit a request at least 45 days before the ceremony.
Which are the main steps of the Root KSK Ceremony?
Once all the attendants are in the ceremony room, the CA and the IW unlock the safe room that contains the two safes with their respective retina scan and access card, so that the SSC can open the safes. As the CA and the IW must be present in the safe room in order to allow the other participants involved to enter the room, the CA2 and IW2 remain in the ceremony room to guarantee dual-occupancy.
Firstly, the Credentials Safe is opened by the Credentials Safe Controller. Inside there are several safe-deposit boxes, each of them contains an operator card and a security permissions card. Three operator cards, which are collected by the COs, are required to unlock the HSM and two keys are required to open each safe-deposit box.
After this, the Hardware Safe Controller opens the safe containing the HSM, a special laptop that can send commands to the HSM, a USB with the logs from previous ceremonies and a DVD to boot the special laptop. The HSM, which securely stores the KSK, can only be accessed with the three operator cards the COs previously collected.
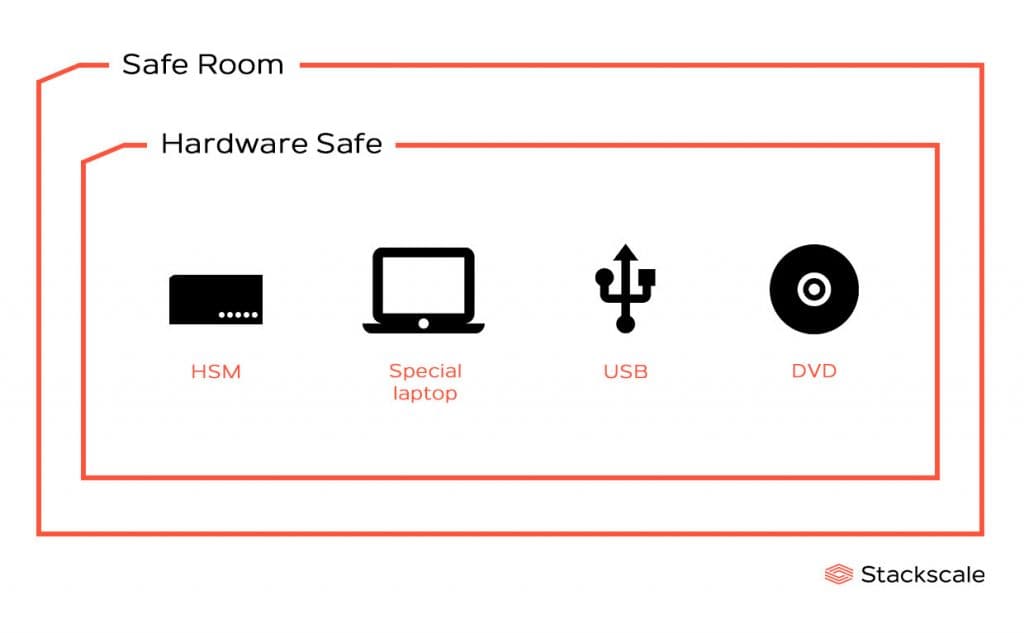
The special laptop has no battery or hard disk in order to eliminate any possibility of the KSK leaving the HSM after completing the ceremony.
To continue with the ceremony, all the equipment collected from the safes is laid out on a table so that all attendants can view it. Then, the COs are called up, one by one, to hand over their operator cards to the CA. They do so after verifying the tamper-evident bags are exactly as they were when they placed them back into the safe-deposit boxes at the end of the previous ceremony.
Once the CA has the operator cards, he boots the special laptop from the DVD, initializes the USB and, then, places the three operator cards into the machine to activate the HSM. After these steps, the HSM is connected to the special laptop via ethernet cable and the CA gets access to the KSK.
He loads the KSK request into the special laptop via USB and, to guarantee that the right key is being signed, a PGP hash of the KSK request is computed and Verisign verifies the key is identical to the one they provided.
Finally, the CA signs the Key-signing Request (KSR) with the private KSK and enters “Y” on a command and the most complex part of the ceremony is completed. The KSR contains a group of Zone-signing Keys, enough to last the quarter until the following ceremony, that are rotated out every 15-16 days.
As we have mentioned before, everything is recorded by auditors and videotaped to reinforce trust. After all, keeping the Internet secure affects virtually everyone nowadays.
Where does the Root KSK Ceremony take place?
The Root Signing Ceremony takes place, alternately, in El Segundo, California (USA), and Culpeper, Virginia (USA). These are the two locations that safeguard the Key-signing Key. Both locations are secure facilities and contain redundant copies of the KSK.
When does the Root KSK Ceremony take place?
The Root Key-signing Key Ceremony usually takes place quarterly in one of the two geographic locations mentioned above. The last ceremony, Root KSK Ceremony 42, took place on 11 February 2021 at El Segundo, California.
Root KSK Ceremony 42 video
Sources: The DNSSEC Root Signing Ceremony by Cloudflare and Key Ceremony Roles by IANA