When migrating to the cloud, security must be taken into consideration from the beginning. By preparing a secure migration to the cloud, you will not only avoid many risks, but also save a lot of time and money. There are many factors to consider when migrating to the cloud, from your company’s current security measures to regulatory requirements and cloud security best practices.
For ensuring a smooth and successful migration it must be planned carefully, so that data and applications will not be disrupted or that, in case they are, the disruption is minimal. Let’s see some key elements to prepare a secure migration to the cloud.
Designing a custom-made cloud migration plan
As migrations are complex and depend on each project and its requirements, planning is essential for ensuring a secure migration to the cloud. There are many aspects to take into consideration, such as industry regulatory compliance, performance or internal security policies. A proper plan will allow you to determine:
- which applications and data will be moved to the cloud and how,
- which migration strategy and which type of cloud is the most suitable for your company,
- how to reduce risks,
- who will be involved in the migration, etc.
Adapting on-premises security to the cloud
Assess the security measures on your current on-premise infrastructure in order to adapt them to cloud security best practices and standards. This way you will avoid data losses and disruptions, both during and after the migration. Moreover, it is recommended to adopt open standards and protocols to ensure interoperability and data portability and avoid vendor lock-in. In addition, to minimise data breach risk, it is also important to determine which team members will be given access to the data and applications in the cloud.
Meeting regulatory requirements
Regulatory compliance is essential when planning a migration to the cloud. This is specially important for highly regulated industries, such as finance and healthcare. So, when migrating to the cloud, you must carefully evaluate which regulatory requirements apply to your data in order to avoid penalties. Your cloud provider can help you meet regulatory requirements if necessary, but you must take the time to assess any particular requirements.
For highly regulated industries, a Private Cloud environment is usually the logical choice to comply with the regulations, as it offers a high level of security and privacy. In a dedicated cloud environment, companies do not share their resources with other customers. Moreover, when assessing security requirements for moving to a cloud environment, you must check the infrastructure you are migrating to meets security standards and is located in highly-secure data centers, certified by international standards.
Understanding the shared-responsibility model
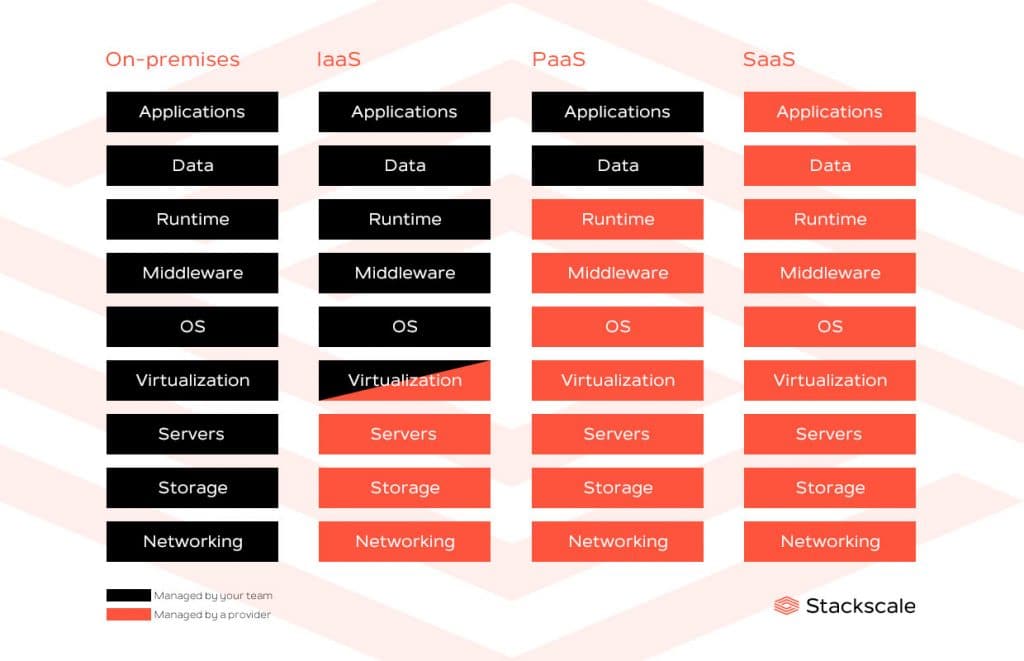
When migrating to a cloud environment, you must always keep in mind that security is a two-way street. The cloud is based on a shared-responsibility model where the Internet Service Provider (ISP) is responsible for the security of the cloud and the customer is responsible for the security in the cloud. The following infographic shows what is managed by the cloud provider and what is managed by the customer in the different cloud service models:
Encrypting data and using secure protocols
Make sure all your data is encrypted and use secure protocols such as HTTPS for data transfer. Actually, data should be encrypted both at rest — while it is sitting in one place — and in-transit — while it is moving between several locations. This applies to ensure maximum security both on-premises and in the cloud.
Ensuring a clear and efficient communication
Last but not least, as for any project, communication plays an essential role in its success. You should ensure a clear and efficient communication among all parties involved in the migration, from decision makers to IT specialists, legal teams and security managers. By discussing needs, goals and threads among all the parties involved, it will be easier to create a successful migration strategy. This way, companies can avoid disruptions, data losses and other potential risks more effectively.
As mentioned on Cisco’s 2018-2023 Annual Internet Report, according to the Uptime Institute, half of all workloads will be run outside the enterprise data center by 2021. So, security is essential for avoiding risks such as DDoS attacks, cloud malware injections, cloud-API attacks or service hijackings. The security measures to implement will depend on different factors, like the chosen cloud solution or industry regulatory requirements.
If you are looking forward to migrating your infrastructure to the cloud, do not hesitate to contact our cloud experts for advice. We can help you plan your migration to the cloud.