SSH, short for Secure Shell, is a remote administration and network protocol; originally designed to replace Telnet and other unsecured protocols such as the Berkeley Remote Shell (rsh). SSH enables secure remote system administration and file transfer over unsecured networks. In this article we will talk about the SSH protocol and its versions, SSH clients and servers, implementations, usage, etc.
What is the SSH protocol and what is it used for?
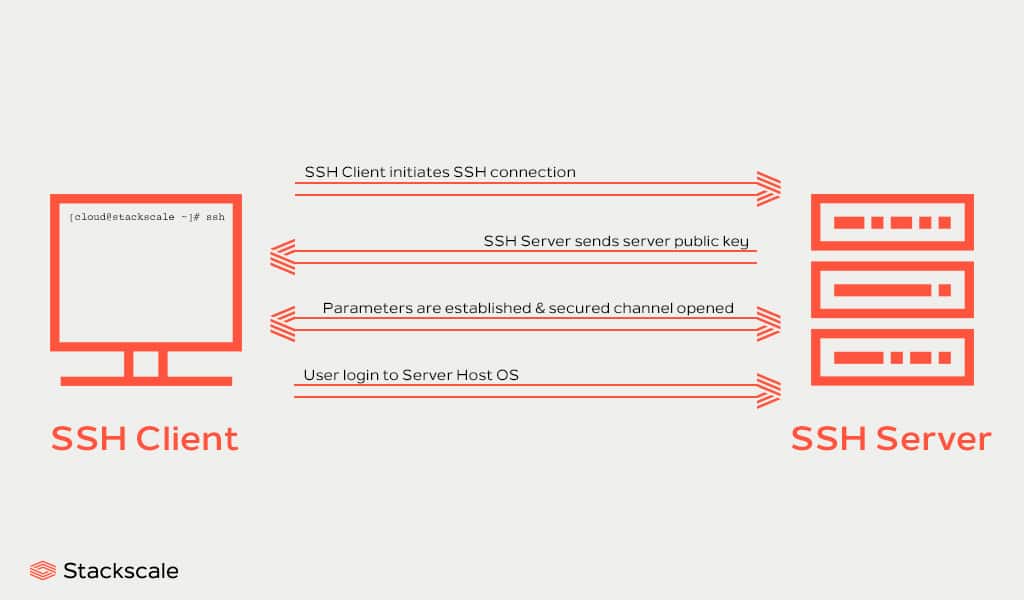
The SSH protocol is used for securing network services over an unsecured network. It is used in almost all data centers nowadays. Secure Shell uses a client-server architecture to provide a secure channel over an insecure network. As defined by The Internet Society document describing the architecture of the Secure Shell (SSH) protocol:
“The Secure Shell (SSH) Protocol is a protocol for secure remote login and other secure network services over an insecure network.”
This cryptographic network protocol is used for securing all kinds of network services. It uses encryption to secure the connection between the SSH client and server, protecting against attacks in the network. SSH allows accessing command lines, executing commands, logging in and performing sysadmin tasks remotely and securely. Besides, the SSH protocol is also used in diverse file transfer mechanisms. For instance:
- SFTP (SSH File Transfer Protocol; a secure alternative to FTP).
- FASP (Fast and Secure Protocol).
- SCP (Secure copy).
The protocol’s encryption aims to provide strong data confidentiality and integrity. SSH uses public-key cryptography for its authentication mechanism — known as “public-key authentication”. Besides, it also supports password-based authentication.
Main ways to use SSH
- Using automatically generated public-private key pairs to encrypt a network connection and log in using a password.
- Using manually generated public-private key pairs to perform the authentication. This way users and programs can log in without a password.
Unknown public keys must always be verified in all SSH versions before being accepted as valid; in order to avoid authorizing an unauthorized attacker as a valid user.
SSH and cloud computing
In cloud computing, SSH is useful for solving connectivity problems and avoiding security issues. An SSH tunnel can provide a secure path over the Internet, through a firewall, avoiding the exposure of virtual machines directly on the Internet.
SSH clients
A SSH client is a software that uses the Secure Shell protocol to connect to a remote computer.
Examples of SSH clients
Here are some examples of SSH clients:
| SSH Client | Developer | Released | Latest release | Current version | License |
|---|---|---|---|---|---|
| SecureCRT | VanDyke Software | June 1998 | September 2021 | 9.1 | Proprietary software |
| OpenSSH | The OpenBSD project | December 1999 | August 2021 | 8.7 | BSD |
| ZOC Terminal | EmTec, Innovative Software | July 1995 | August 2021 | 8.02.7 | Proprietary software |
| PuTTY | Simon Tatham | January 1999 | July 2021 | 0.76 | MIT |
| wolfSSH | wolfSSL | July 2016 | July 2021 | 1.4.7 | GPLv3 and proprietary software |
| Bitvise SSH Client | Bitvise Limited | 2001 | July 2021 | 8.49 | Proprietary software |
| Tera Term | TeraTerm Project | 2004 | June 2021 | 4.106 | BSD |
| TtyEmulator | FCS Software | May 2002 | March 2021 | 4.6.0.0 | Proprietary software |
| Dropbear | Matt Johnston | April 2003 | October 2020 | 2020.81 | MIT |
For further examples and details about existing SSH clients, you can visit Wikipedia’s comparison of SSH clients.
SSH servers
A SSH server is a software that uses the Secure Shell protocol to accept connections from remote computers.
Examples of SSH servers
Here are some examples of SSH servers:
| SSH Server | Developer | Released | Latest release | Current version | License |
|---|---|---|---|---|---|
| OpenSSH | The OpenBSD project | December 1999 | August 2021 | 8.7 | BSD |
| Bitvise SSH Server | Bitvise Limited | 2001 | July 2021 | 8.49 | Proprietary software |
| wolfSSH | wolfSSL | July 2016 | July 2021 | 1.4.7 | GPLv3 and proprietary software |
| Apache MINA SSHD | Apache Software Foundation | 2009 | May 2021 | 2.7.0 | Apache 2.0 |
| CopSSH | Itefix | August 2003 | March 2021 | 7.5.0 | Proprietary software |
| CrushFTP Server | CrushFTP, LLC | January 2003 | February 2021 | 10.0.0 | Proprietary software |
| Teleport | Gravitational | June 2016 | May 2021 | 6.2 | Apache 2.0 |
| Dropbear | Matt Johnston | April 2003 | October 2020 | 2020.81 | MIT |
For further examples and details about existing SSH clients, you can visit Wikipedia’s comparison of SSH servers.
Versions of SSH
The specification of the SSH protocol includes two major versions: SSH-1 and SSH-2. Version SSH 1.99 is also worth mentioning, although it is not a version as such.
SSH-1
The first version of the SSH protocol was SSH-1. SSH-1 was designed by the Finish researcher at Helsinki University of Technology, Tatu Ylönen, in July 1995. Tatu Ylönen decided to create this first version of the SSH protocol after a password-sniffing attack at his university’s network. Its goal was to provide strong authentication and confidentiality, as opposed to that offered by already existing protocols — rlogin, Telnet, FTP and rsh.
SSH-1 was released as a freeware and quickly gained in popularity. As a result, by the end of 1995, the researcher founded SSH Communications Security to further develop and market SSH. So, while the original version was mainly composed of free software, the later versions included an increasing number of proprietary software.
SSH-2
SSH-2 is the second version of the SSH protocol. Its development was undertaken by a working group officially called “Secsh” by the IETF (Internet Engineering Task Force). The version 2 of the Secure Shell protocol was adopted as a standard in 2006 and is incompatible with the previous version, SSH-1. SSH-2 includes new features and security improvements, for instance: integrity checking using message authentication codes and the ability to run any number of shell sessions over a single SSH connection.
SSH 1.99
According to the RFC 4253 specification, SSH servers supporting both SSH-1 and SSH-2 should identify its protoversion as SSH 1.99, in order to identify backward compatibility.
Popular SSH implementations
OpenSSH, PuTTY and Tectia SSH are some of the most popular SSH implementations. Although, as shown in the tables of SSH clients and servers above, there are many options available.
OpenSSH, short for OpenBSD Secure Shell, stands out as one of the top open source implementations of the SSH protocol. It is a suite of secure networking applications based on the SSH protocol. Besides, as an odd fact, with the OpenSSH client-server implementation, it is possible to use the SSH protocol to implement a VPN.